Try Hack Me Room Brute It
Et Tu, Brute It?
Task 1 About this box
Try Hack Me breaks down our rooms into tasks. Our Task 1 in this room is mostly an introduction to the room and what we hope to learn about while we’re here. We should be learning about -Brute-force -Hash cracking -Privilege escalation I find it useful to write these things down and refer back to it as sometimes we start to think our goal is to fill in all the answers in this room when really our goals should be to better our understanding of the concepts listed above
We also start the machine in Task 1 and then we’re on our way
Task 2 Reconnaissance
Our tasks are further broken down into separate questions and our first question for task 2 is How many ports are open?
How many ports are open?
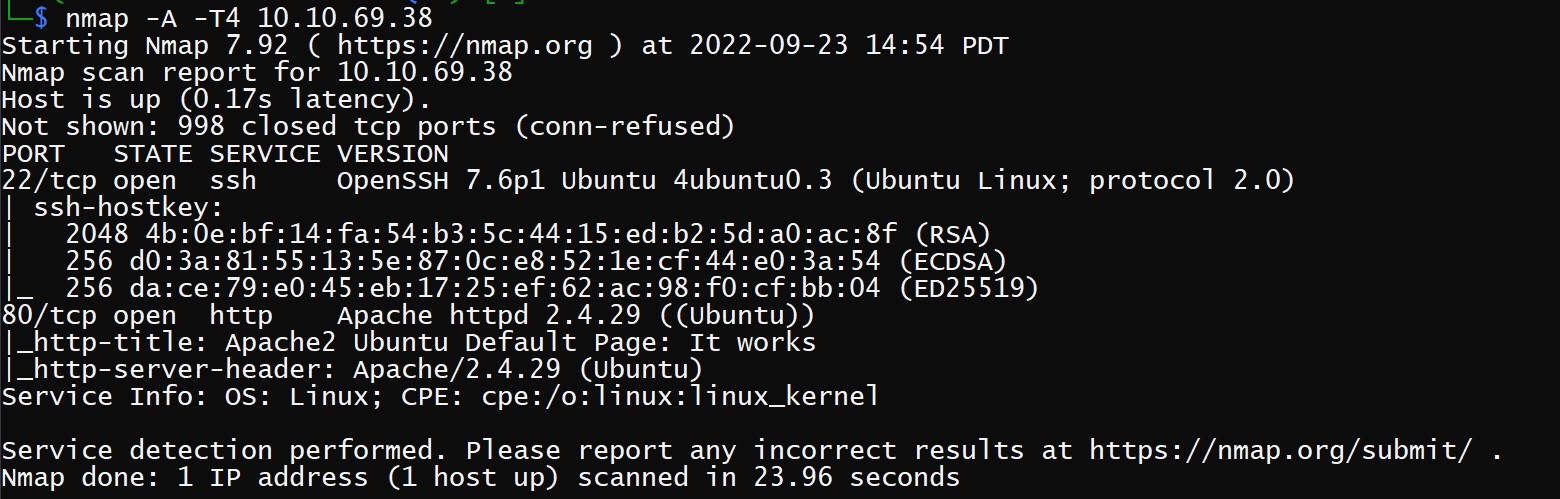
We actually get a straightforward instruction here to use nmap. I followed an example I found on the internet without knowing what the flags are doing. The first command I used was: nmap -A -T4 [TARGET_IP_HERE]
The hint for this question suggest using nmap -sS -sV [TARGET_IP_HERE]. I got the answer I needed and noted down that I should circle back around to understand what the nmap flags are doing on these commands.
The -A flag combines two flags, -O and -sV which gives us operating system information and tries to tell us what services are running on the machine. The -T4 is a timing template, which I understand to mean that T0 is the slowest but most accurate setting and T5 would be the fastest least accurate setting.
To compare this is what we get with only the -T4 flag
What version of SSH is running?
Our nmap scan shows this to be Open SSH 7.6p1
What version of Apache is running?
This is part of why we needed those flags, in the first picture above we can see Apache on port 80 running version 2.4.29
Which Linux distribution is running?
Again something we get from the flags used, it shows Ubuntu as part of the server header and again is referenced in the OpenSSH version name. I assumed I didn’t have this information already so this was a good reminder to note down information in case we need it for later.
Search for hidden directories on the web server. What is the hidden directory?
I used dirbuster to search for hidden file directories. The hint on this suggested using the command gobuster dir -u [TARGET_IP_HERE] -w common.txt, I should do more research but I believe this is just a preference for one tool or the other.
Task 3 Getting a shell
“Find a form to get shell on SSH.”
The way this task is written caused me to feel like I missed some steps, but it’s just summing up the entire Task 3 end result instead of leading you into how to get started. I had to go back and think about what I now had access to and how that was going to achieve the goal of “find a form to get shell on SSH”. The last thing we had done was find the hidden directory at [TARGET_IP_HERE]/admin at the end of task 2.
True to the name of the room we need to take this directory, and use brute it, using a brute force tool. I couldn’t remember what tools work for when we want to brute force a web form so I searched for “brute force web form kali linux” and the top respones were all how to use Hydra.
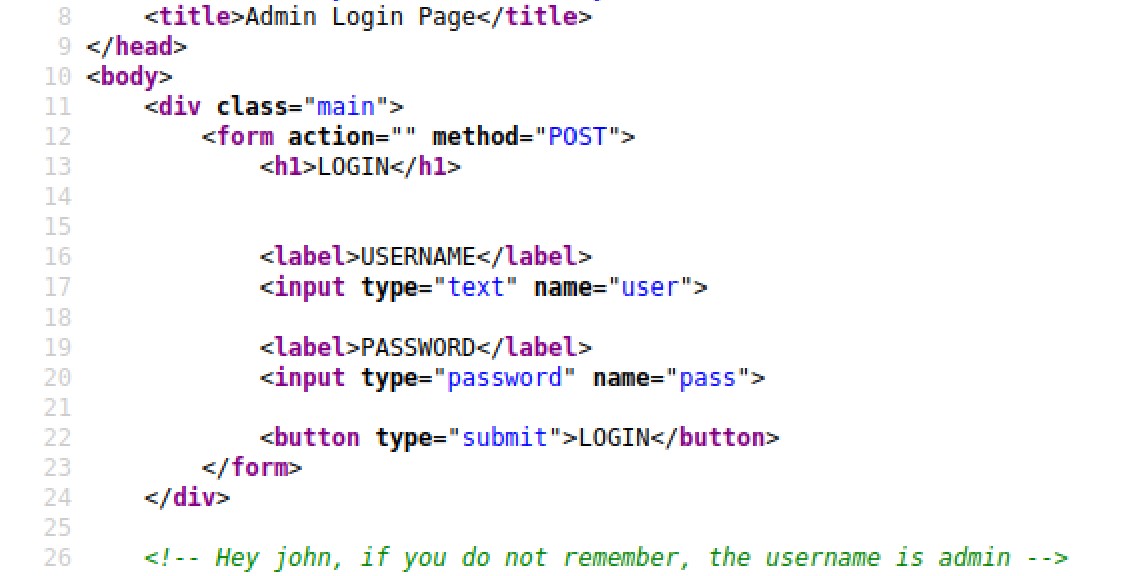
The most ridiculous step in this entire room might be getting the admin account name from a comment in the page source of this hidden admin page. We are given the comment “Hey John, if you do not remember, the username is admin”.
I followed some examples and read a little bit and used the command hydra -l admin -P rockyou.txt [TARGET_IP_HERE] http-post-form “/admin /index.php:user=^USER^&pass=^PASS^:invalid
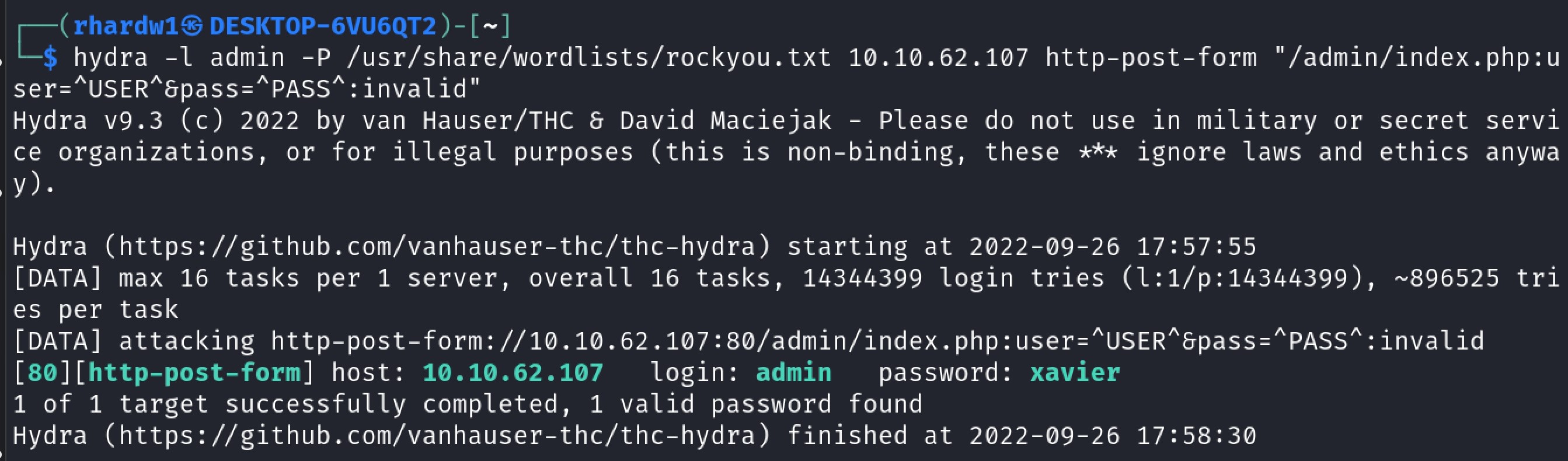
What is the user:password of the admin panel?
Hydra gave us this in the above screenshot, we see our match for admin:password
Crack the RSA key you found. What is John’s RSA Private Key passphrase?
We are given an RSA key when we get in the admin panel. We want to crack this using John the Ripper. We also got the name “John” in relation to the key. My unfamiliarity with the “John the Ripper” software slowed me down considerably here. I wasted 30 minutes before realizing my first step had to be preparing the RSA key with a line like the following: ssh2john.py id_rsa > hash. Then using john with a wordlist, I used the rockyou wordlist. I spent another hour reattempting the brute force and using diffeent wordlists before I realized that the software doesn’t output the cracked passwords when you’re done and you need to open a log file using John the Ripper. We should find that the pass phrase is “rockinroll”.
user.txt
Using the RSA key and cracked pass phrase we can now get on an SSH connection to the server using the following command: ssh -i id_rsa john@[TARGET_IP_HERE]. From here we can get our user.txt flag.
Web flag
We already got this flag back at the website login page. Weird choice to take the answer for it after the user.txt flag but hey whatever, we get to move on to Task 4 now.
Task 4 Privilege Escalation
Coming soon
Find a form to escalate your privileges. What is the root’s password?
Coming soon
